Being compliant means following the intent of the law as spelled out in your industry regulations. These regulations are designed to protect privacy rights, protect transactional information, and prevent fraud. Becoming compliant doesn’t need to be an excessively challenging task. Like most things in life and in business, compliancy can be addressed in a structured and logical way.
The National Institute of Standards and Technology (NIST) provides an integrated approach to cybersecurity whose philosophy is to “build it right” and then “continuously monitor” as a means to providing “near real-time” information to base decision making. Thus, providing better risk management and ensuring compliancy. The guidelines provided by NIST are vendor-neutral and are meant to fulfill all of your security needs.
The SP800-53r4 will help your organization establish baseline controls and tailor those controls according to your needs. This special publication (SP) is the starting point for deciding how to mitigate risks, implement controls, and prove that your controls do indeed mitigate your determined risks.
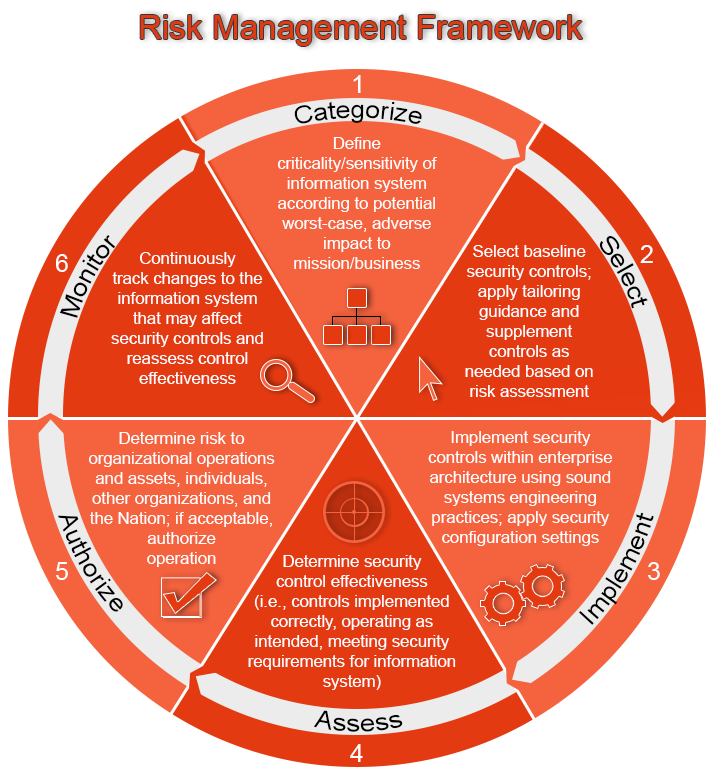
To correctly categorize baseline controls (step 1 of the Risk Management Framework), mission/business owners, authorizing officials, chief information officers, senior information security officers, information system owners, information owners/stewards, and risk executives need to be included in the conversation. These are the folks who can adequately identify relevant laws, policies and best practices that must be adhered to; these individuals also assign responsibilities to individuals/groups for developing, implementing, assessing, authorizing, and monitoring controls.
In order to have a consistent implementation across the entire organization, security controls can be divided into groups such as common, hybrid, and system-specific. Determining which group a control belongs to is a matter of context. For example, a control may be system-specific for a particular information system, but be a common control for another system, which would inherit the control from the first system.
Baseline controls (step 2) are the starting point for selecting security controls; these can be found in the Appendix D of the SP800-53r4. It is your stakeholders’ responsibility to decide what and how to implement these controls in the most cost-effective way.
Viewed conceptually, organizations must be able to describe the core security requirements needed for their mission/business functions. Step 3 involves defining a set of security controls that are properly designed, implemented, and produce the required capability.
When conducting assessments (step 4) on a control-by-control basis, a failure of a single control should not result in the failure of the overall security requirement of a particular system or area. Multiple controls should be implemented to allow for redundancy and to provide a means for the organization to assess the severity of a newly discovered vulnerability.
Step 5 of the Risk Management Framework requires the stakeholders or Authorizing Official(s) to verify that your implementation is sufficient and compliant; these officials are legally held accountable for this. They should also understand what risks remain and have a plan of action for these risks.
The final step (step 6), is the continuous assessment of the implemented controls. This involves documenting changes, performing impact analyses, and keeping your stakeholders informed of the status of the system’s security.
All of this information can be a little daunting so we’ve included a simple graphic to better explain the steps of the Risk Management Framework. If you need help implement the RMF, Cinteot is made of a team of industry leading experts. Actually, we even wrote the original documentation for it! Connect with us or read more about our services.