Early on, Cinteot personnel wrote the Database Security Requirements Guide (SRG) and Database Security Technical Implementation Guides (STIGs) for DISA’s Field Security Office. Since those days, Cinteot has invested many hours of security training in its employees. We’ve built templates for system security documentation that have been tested in multiple C&A and Corporate IT Security Reviews in both DoD and DHS. We have certified DISA reviewers on staff to assist in CCRI and C&A prep.
System Hardening is the practice of increasing security of a system and all its subsystem components, to meet compliance while maintaining adequate operations. Examples of traditional components are Network, Server, Database Management System, and data. As organizations expand their operations out to various Cloud (and other) Service Providers, an already broadly scoped discipline with much complexity has increased dramatically. Deep expertise is required in each subsystem component as well as various tools to assist with compliance auditing.
Cinteot retains a rapid response Cybersecurity Response Team who can address required hardening as part of a comprehensive Cinteot SRR (System Readiness Review) or as part of a more targeted approach pending the situation (e.g., post-incident Database Hardening).
In addition to our broadly scoped Cybersecurity competencies, we have experts who can ‘deep dive’ sub-components. Some examples include:
•Network Hardware
•Standalone Servers
•VPN
•Telecom Services
•Virtual Servers
•Cloud-based ‘as a Service’ appliances
•Firewalls | Routers
•Physical Security
•Auditing
•Secure Storage
Our team is well versed in major Cloud Service Providers such as AWS, and Azure and their respective native services. As part of our overall Cloud Governance Assessment, or separately, we can help you get a handle on configuring your cloud environment to control service-provisioning; configure targeted cloud services; and devise and implement an auditing strategy.
Cybersecurity Risk Management Framework
The NIST RMF (Risk Management Framework) has gradually become the preeminent governance model for securing assets in a repeatable, measurable manner (It is now the standard Risk Framework within the Department of Defense).
The overall guiding principle in adopting the RMF, or a Risk Based Mentality in general, is to secure systems and assets utilizing effectively allocated resources. It is not enough to simply secure systems. There must be a firm grasp of what to secure and to what extent. The RMF guides us through the steps and provides guidance to identify all assets and systems and measurably secure them through repeatable processes.
Cinteot is home to a team of best-in-class Risk Management Practitioners as well as a wide range of Technical and Subject Matter experts who can support adoption and application for a broad variety of organizations. Our team can take you through all the seven steps (below), while advising on how to evaluate each asset and system. Our team ensures a thorough understanding of all assets and systems. We conduct a Business Impact Analysis and a Threat Analysis as part of our standard approach. Our team has deep expertise in mapping NIST Security Controls so that our System Hardening Experts have clear guidance to work from.
We understand that Data Assets can be particularly challenging assets to inventory and categorize. Our team of Data Architects and Data Scientists have the appropriate expertise to help you catalog and understand your Data Assets. They will then subsequently adapt them to a mature Data Governance framework.
Security Reviews Undergoing an independent Security Review is a critical step towards protection of assets and gaining the necessary compliance to operate.
Cinteot conducts a range of reviews from specified needs to full scope assessments. We conduct our full scope reviews by exploring all possible attack vectors. This typically involves discrete systems in addition to corporate culture and business strategy, and stakeholders. Our expert level Risk Management Practitioners will ensure that all potential vulnerabilities are assessed within the context of their effects on business objectives.
Cinteot brings a wealth of experience and ‘lessons learned’ from the numerous reviews we have conducted in the past. We are accustomed to dealing with compliance requirements from multiple entities. Our highly trained and certified cybersecurity practitioners will guide you through the process and assist you in developing a post-review course of action.
A key part of our comprehensive SRRs (Security Readiness Reviews) is to ensure STIG (Security Technical Implementation Guide) compliance. STIGs, Developed by DISA, specify a reference point and best practices for how to secure IT Assets for CSM (Configuration Management Settings) by providing detailed configuration guidance for a wide array of hardware and software assets.
Navigating the world of STIG compliance can be overwhelming within a Federal IT organization. Within DISA there are hundreds of STIGS addressing a wide variety of configurable assets. While STIGs offer welcome guidance which would be daunting to otherwise define on your own, maintaining full compliance still involves significant expertise and knowledge. Each asset presents a unique challenge, and a single oversight can put you out of compliance, or worse, result in a serious compromise of Confidentiality, Integrity, or Availability.
Cinteot’s Cybersecurity specialists have broad knowledge and experience of the CSM landscape, DISA STIGS and Risk Scoring. In addition, Cinteot has deep expertise in several of the assets typically addressed by STIGS.
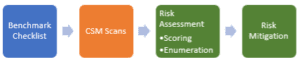
Cinteot will navigate you through the entire process, to include Establishment of Security Configuration Benchmark Checklist (NIST SP 800-70), CSM Scans (utilizing a variety of tools), Risk Enumeration and Prioritization, and Risk Mitigation.
Cinteot also offers Training programs to help get your team up to speed on the overall SRR, CSM and SITG compliance processes. Cinteot instructors can lead SRR classes in relevant technologies and application of auditing tools. Instructors would then administer exams to test students’ learned skills as required for validation and verification of STIG/IAVA compliance. Additionally, Cinteot Senior Reviewers can provide on-the-job training and check rides to new reviewers to fully vet them before establishing their reviewer readiness level.
Certification and Accreditation
Cinteot has a full service offering in Certification and Accreditation. Performed as an augmentation to our Security Reviews our C&A process ensures that an organizations systems are fully prepared with formal cybersecurity compliance. Our C&A reviews involve a full written Risk Assessment which will identify all compliance requirements and associated security controls. Our team of DISA Reviewer Certification Program (RCP) certified reviewers have a depth of experience in developing compliance strategies for required security controls. This typically not only involves knowledge of the controls themselves but deep systems knowledge over a wide range of architectural patterns which span both IT Infrastructure and Applications.
Our competencies in STIG compliance, Penetration Testing, Log Analysis and Configuration Management enables our team to perform a full scope independent audit of your system(s). Thus, we can offer advisement for remediation of any identified vulnerabilities which present an unacceptable risk for your compliance.